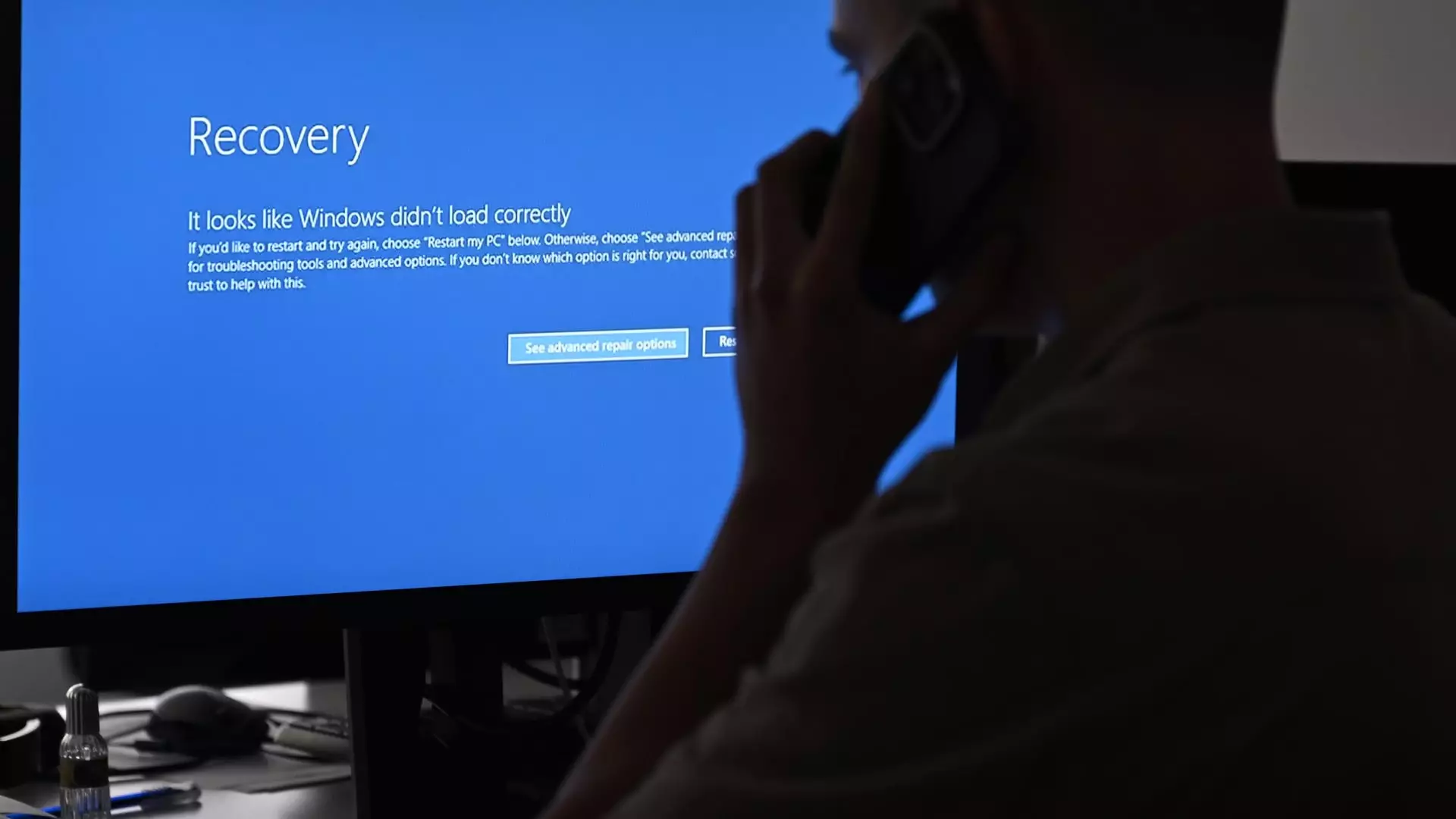
When computer screens turned blue on a global scale, the consequences were far-reaching. Flights were grounded, hotel check-ins were impossible, and freight deliveries came to a halt. The initial reaction was to suspect a cyberterrorist attack, but the truth turned out to be a botched software update by the cybersecurity company CrowdStrike. This incident highlighted the critical role that IT plays in our modern society and the catastrophic effects that a single mistake in the digital realm can have.
The botched content update by CrowdStrike affected a wide range of customers globally due to the company’s broad base of clients. The update was linked to the CrowdStrike Falcon monitoring software, which monitors endpoints for malware and other malicious activities. The automatic update feature rolled out buggy code, leading to a cascade of problems across various organizations. This incident underscored the interconnected nature of IT systems and the severe repercussions of a flawed software update.
In the aftermath of the global IT outage, cybersecurity experts pointed out several key lessons. One crucial aspect highlighted was the need for companies like CrowdStrike to roll out updates incrementally rather than pushing them out to everyone at once. Testing updates in different environments and implementing quality control measures are essential to prevent such failures in the future. The incident also shed light on the importance of building redundancy into IT systems to mitigate the impact of single-point failures.
The Friday meltdown served as a wake-up call for businesses to reassess their cybersecurity strategies. Rather than viewing cybersecurity services as a cost, organizations should consider them as a vital investment in their future. Building redundancy into enterprise systems, although costly, is essential to prevent disruptions like the one caused by the botched software update. Business owners must recognize the significance of cybersecurity and allocate resources accordingly to safeguard their operations.
Cybersecurity experts emphasized the need for accountability and preparedness in the face of potential vulnerabilities. Kernel-level code, like the one that caused the recent disruption, requires rigorous scrutiny and separate approval and implementation processes to ensure system integrity. With an ecosystem filled with third-party vendor products, identifying vulnerabilities and fortifying systems against cyber threats remains a complex challenge. Investing in backup and redundancy is crucial, even if businesses argue about the costs, as the consequences of a cybersecurity breach far outweigh the expenses of preventive measures.
Overall, the botched software update incident serves as a stark reminder of the interconnected and fragile nature of modern IT systems. It underscores the need for organizations to prioritize cybersecurity, resilience, and redundancy to safeguard against potential disruptions. By learning from past mistakes and implementing robust cybersecurity measures, businesses can better protect themselves from future cyber incidents. It is imperative for businesses to view cybersecurity not as an option but as a critical component of their operations to ensure continuity and security in an increasingly digital world.